
Antid0te UG is an international IT security company based in Cologne/Germany. We are specialised in identifying weaknesses and security vulnerabilities in desktop, web and mobile applications. Furthermore we develop security tools for use by researchers and end users.
We offer a full range of services. This includes vendor-independent consulting, security audits and training courses.
We possess specialised know-how in the field of MacOS/iOS.
Antid0te UG is also committed to the field of security research and our consultants are sought-after speakers at national and international conferences.
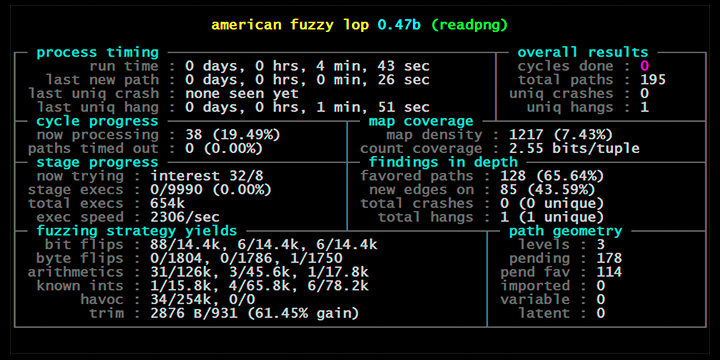
Antid0te is releasing an online on demand MacOS and iOS Userpace Fuzzing Training Course.

For a limited time Antid0te is offering the special Training Unlimited Promotion again that allows subscribers to attend all four of our training courses for a very special price.
Antid0te is organising an online MacOS and iOS Kernel Internals For Security Researchers Training Courses in June 2023.

Antid0te is organising an iOS 16 and MacOS Userspace Exploitation Training Course in April 2023.

Antid0te is organising an iOS and MacOS Kernel Exploitation Training Course in Singapore in May 2023.

Please enjoy our MacOS and iOS Security Internals Advent Calendar video series over at YouTube. Featuring one new video every day until christmas 2022.
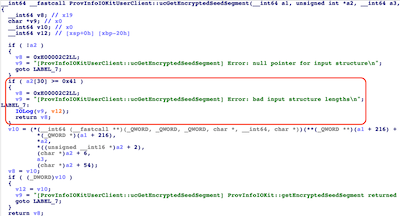
A dive into the iOS kernel to track down CVE-2019-7287 that is said to be exploited in the wild...
Training "MacOS and iOS Kernel Internals for Security Researchers" for EU/North America Timezones
Training "iOS and MacOS Kernel Exploitation" in Singapore
Training "iOS and MacOS Userspace Exploitation" in Singapore
Training "Practical MacOS Kernel Exploitation on ARM64" for EU/North America Timezones
Video Playlist "MacOS and iOS Security Internals Advent Calendar".